Risk Definitions and Identification
Risk Management is the foundation for all security decisions.
ISRM: Information Security Risk Management⌗
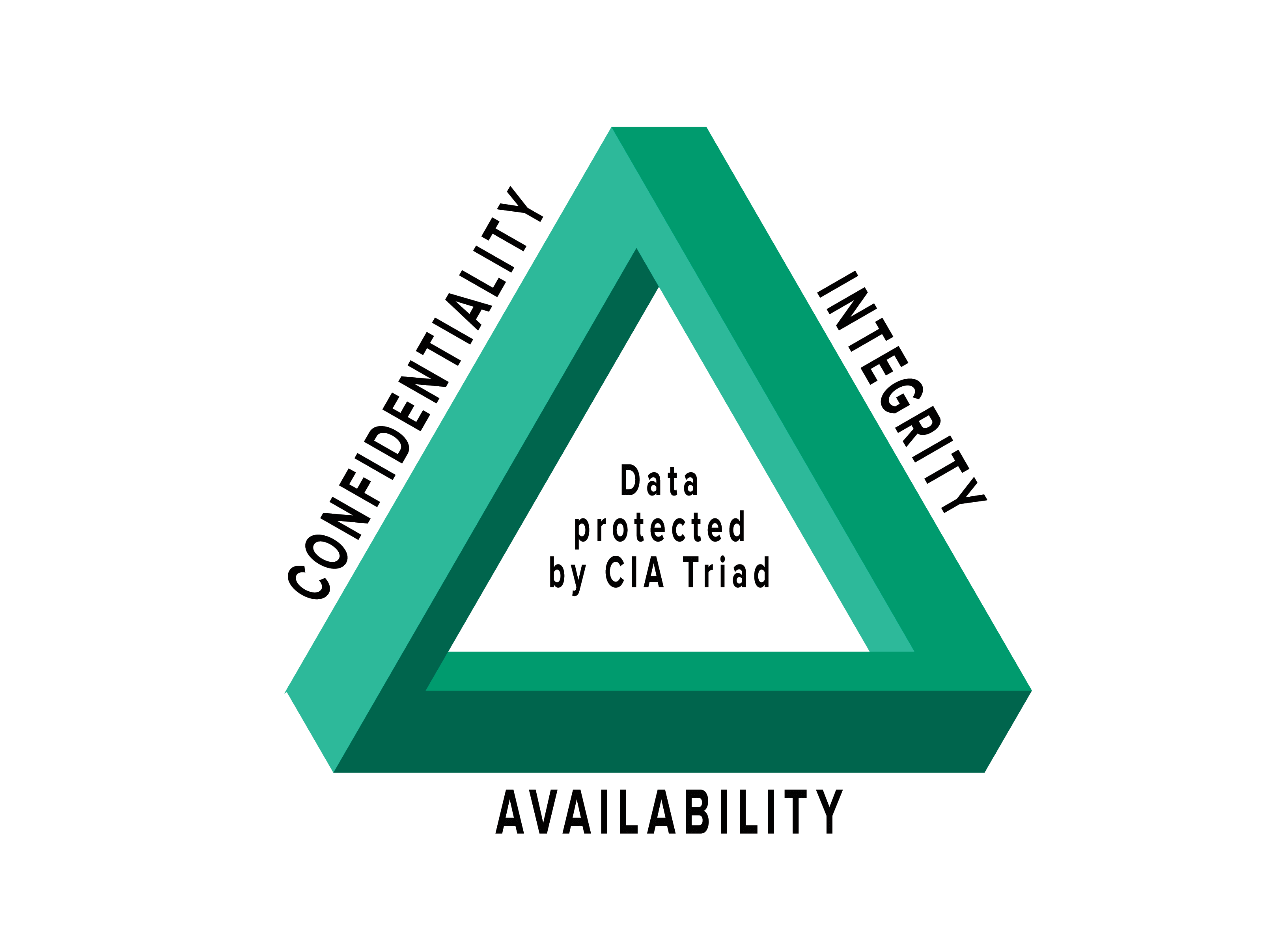
ISRM, or Information Security Risk Management is the process of managing risks associated with the use of information technology. It involves identifying, assessing, and treating risks to the confidentiality, integrity, and availability of an organization’s assets.
Managing risks associated with the IT/CIA Triad
Risk Definitions⌗
Lingo for identifying risk. For the CISSP, you need to be solid on definitions since organizations use of terms can shift a bit.
- Asset: Anything of Value to the Company
- Beyond just the price of the physical asset.
- Value Intellectual information, potential fine if mismanaged, Reputation, many elements add value to asset.
- Vulnerability: A weakness the absence of a safeguard
- Are there weaknesses in the asset? “Absence of a safeguard”
- Threat: Something that could pose loss to all or part of an asset
- Poses harm to asset.
- Exploit: An instance of compromising an asset with a vulnerability
- Risk: The probability of a threat materializing
- Controls: Physical, Administrative, and Technical Protections
- Safeguards are Proactive (Firewalls)
- Countermeasures are Reactive (Auditing incident logs)
- Total Risk: The risk that exists before any control is implemented
- Inherent risk that always exists, with everything before implementing countermeasures.
- Countermeasures and Safeguards reduce total risk by implementing controls.
- Residual Risk: Leftover risk after applying a control
- Risk cannot be eliminated. Work on bringing down the amount of risk => Residual risk.
- Risk management is about getting down to an acceptable Residual Risk level.
- Secondary Risk: When one risk response triggers another risk event
- When one risk response, triggers another risk event. Damned if you do, damned if you don’t.
- Risk fix: pull down a patch, creates a secondary risk due to bugs caused by patch.
- The “unknown” risks which occur
- Incident: A Risk event that has transpired
- Will probably result in an Audit/Post Mortem
eg: Data is an asset, Vulnerability: is weak passwords protecting data, Threat: agent could compromise passwords, Threat Agent: attacker + software to crack passwords, Exploit: When it happens, Risk: Probability that it will happen if no mitigation action is taken. Fix: Implement mitigation using password strength or MFA to safeguard assets.
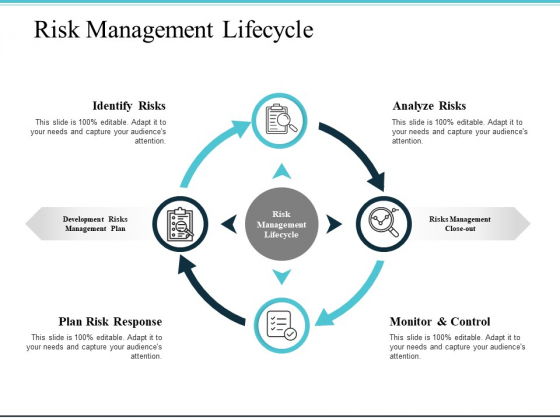
Risk Management Steps⌗
Revolving lifecycle which doesn’t end.
Risk Identification⌗
- Identify Assets
- What are we protecting?
- What is their value? Informs later decisions.
- Identify Threats
- What would harm our Assets?
- Identify Existing Controls
- What is currently in place?
- There are probably already policies in place, what vulnerabilities are left?
- Identify Vulnerabilities
- Identify Consequences
- Feeds into Risk Assessment
Methods to Identify Risk⌗
Millions of ways to identify risks. You need to do research to discovery risks. Part of the job is to do due-diligence and research risks
- Sources of Risk Documentation
- Audit reports / Incident Reports
- Interviews with SMEs, Public media
- Annual reports
- Press releases
- Vulnerability assessments and penetration tests
- Business continuity and disaster recovery plans
- Interviews and workshops
- Threat Intelligence Services
Alignment with Business Goals and Objectives⌗
Risks are only relevant as they impact the business. Look at risks which impact the business’s alignment.
Everything aligned with the business, everything supports the business.
Look beyond the technology, understand the business goals.
- The first and most important step for CISM is to understand the business. Review organizational vision and strategy first.
- Look beyond IT–Risk is measured by the impact the risk has on the business, not a particular system.
- In order for risk to be integrated into the enterprise, senior management must be supportive and involved.
- If management funds and supports the risk management processes we will have what we need to be successful.
- Good metrics mean that we have attainable objectives which will help us accomplish our goals.
- Good communication and transparency helps us make risk-aware business decisions.
Work with management to show that security will proactively support the business’s goals.
Organizational Structures and Impact on Risk⌗
- Risk Context
- What is the context in which you operate? eg: Military culture; lots of constraints and high risk actions which impact human lives.
- Every Org is different, and assumes different risks.
- Risk management approach should be enterprise wide and a common framework should be shared across all departments.
- Framework, Strategy, Programs should be universal across departments.
- RACI Charts can be used to indicate responsibilities.
Three lines of defense
- First Line: Business units
- Oversee and challenge risk management
- Provide guidance and direction
- Follow a risk process
- Develop risk management framework
- Second Line: Risk and Compliance
- Involved in day-to-day Risk Management
- Apply internal controls and risk responses
- Dealing with the systems and information;
doing the work
- Third Line: Audit
- Review 1st and 2nd lines
- Provide an independent perspective and challenge the process
- Objective and offer assurance
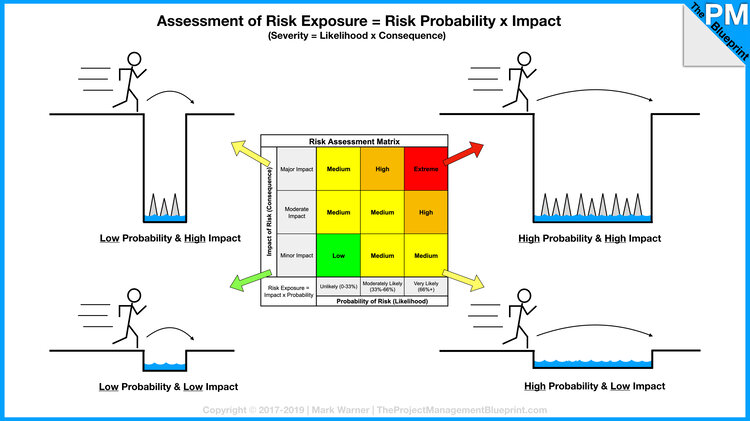
Risk Assessment (Value)⌗
Provide Justification of the mitigation strategies.
Assessment and Analysis terms can be used somewhat interchangeably. Ultimately providing a value of risk.
- Qualitative Value
- Starting point for leading to Quantitative analysis. eg: Brainstorming
- Subjective analysis to help prioritize probability and impact of risk events.
- May use Delphi Technique.
- Wiki The Delphi method or Delphi technique (/ˈdɛlfaɪ/ DEL-fy;[contradictory] also known as Estimate-Talk-Estimate or ETE) is a structured communication technique or method, originally developed as a systematic, interactive forecasting method which relies on a panel of experts.[1][2][3][4] The technique can also be adapted for use in face-to-face meetings, and is then called mini-Delphi or Estimate-Talk-Estimate (ETE). Delphi has been widely used for business forecasting and has certain advantages over another structured forecasting approach, prediction markets.
- Quantitative Value
- Providing a dollar value to a particular risk event.
- Much more sophisticated in nature, a quantitative analysis if much more difficult and requires a special skill set.
- Business decisions are made on quantitative analysis.
- Can’t exist on its own. Quantitative analysis depends on qualitative information.
Qualitative Assessments
Assess risks based on subjective input. Uses terms high, medium, and low. Inexpensive and quick way to begin prioritization and ranking of risks.
Quantitative Analysis
Allows for making good business decisions.
- More experience required than with Qualitative
- Involves calculations to determine a dollar value associated with each risk event.
- Business Decisions are made on this type of analysis
- Goal is to the dollar value of a risk and use that amount to determine what is the best Control for an Asset
- Necessary for cost/benefit analysis.
Quantitative Analysis Formulas and Terms
The math and formulas; stop and think about what the terms me.
What we’re trying to figure out SLE and ALE are the most important.
- AV: Assign Asset Value: Dollar figure that represents what the asset is worth to the org
- EF: Exposure Factor: The percentage of loss that is expected to result in the manifestation of a particular risk event.
- eg: Fire risk on a building.
- SLE: Single Loss expectancy: Dollar figure that represents the cost of a single occurrence of a threat instance
- How much does it cost me?
- eg: Fire in building, $300k asset, looses 50% of value = $150k loss every fire.
- Asset value and Exposure Factor = Value of what you’re protecting
- How much does it cost me?
- ARO: Annual Rate of Occurrence: How often the threat is expected to materialize
- Probability of a risk event happening.
- eg: Fire in building every 10 or 20 years.
- ALE: Annual Loss Expectancy: Cost per year as the result of the threat
- Much more manageable for estimating low occurrence events.
- eg: There might be a fire every 10 years in $300k building, 150k/10years = 15k per year
- eg: Hard drive fails 3x per year = $9k losses. -> Spending $5k to mitigate is worthwhile.
- TCO: Total Cost of Ownership is the total cost of implementing a safeguard. Often in addition to initial costs, there are ongoing maintenance fees as well.
- Includes costs up-front of product and operation costs.
- ROI: Return on Investment: Amount of money saved by implementation of a safeguard. Sometimes referred to as the value of the safeguard/control.
- Implement Controls which are cost effective to potential Risks.
Ultimately: Look at cost of mitigation, up against Annual loss.
Risk Management Life Cycle⌗
Risk Mitigation and Response⌗
Risk assesment dictates appropriate response.
- Reduce
- Avoidance
- Transfer
- Accept
- Reject (Not Acceptable)
Risk Reduction/Avoidance⌗
Actions taken to lessen the frequency and/or impact of a risk. May require usage of several controls to reach levels of risk acceptance or tolerance.
You can’t reduce the chance of rain, but you can take an umbrella to reduce impact of the weather.
The ultimate Risk reduction is Avoidance
- Examples of risk mitigation
- Strengthen risk management practices. Implement sufficeiently mature risk management processes.
- Deploying new technical, management or operational controls that reduce eitehr the likelihood or impact of an adverse event.
- Installing new access control system (ACS)
- Implementing policies or operational procedures
- Developing an effective incident response and Business Continuity Plan(BCP)
- Using compensating controls.
Risk elimination is automatically wrong. It cannot be done.
Risk Transference⌗
The decision to reduce (potential) loss through sharing risk with another organization.
Share potential loss with another organization. Fire insurance for a building, does not lower risk.
- SLAs and contracts establish degree of transference.
- Outsourcing risk; to contract for compliance.
Liability cannot be transfered.
Transferring risk may grant restitution for damages in case of breach, but will not your organization from liability.
Risk Acceptance⌗
Ultimately, accepting risk means there is no active response. Justification must be supplied when accepting risks.
- Examples
- Provide no active mitigation
- Based on cost/benefit analysis; prohibitive cost of control is more than potential for loss
- Acceptance is the only choice(no available method to avoid or reduce)
- Risk acceptance includes due diligence; can be used to indicate good business decisions were made. Paper trail for reasoning not to respond based on information at the time.
- In case of a breach, recording reasoning why risk was accepted will protect agains liability. If there was no due diligence, then you are liable for risk rejection.
- Level of risk and impact is always changing
- Regular reviews are required.
Risk: mitigate, mitigate, mitigate, until risk falls into acceptable levels.
Risk & Controls; Monitoring and Reporting⌗
On a yearly basis analyze the current threats against the organization’s risks. What are the threats today? What’s the probability and impact of a compromise? What mitigations can be applied? Re-assess previous mitigations and solutions based on current threats.
-
A Risk Response is designed/implemented based on a Risk Assessment.
-
Ongoing Monitoring and Reporting of Risk
- Necessary because Controls can become less effective.
- Operational environment changes; new threats, technologies, and vulnerabilities may emerge
-
Monitoring
- Are the risks expected materializing?
KRI: Key Risk Indicators⌗
Alert or warning sign of risks. Good indication that a risk may materialize. (Dark clouds, thunder, lighting may indicate rain is coming)
- Provide early warning
- Provide backward-looking view on risk events
- Enable documentation and analysis of trends
- Provide an indication of risk appetite and tolerance
- Increase the likelihood of achieving strategic objectives
- Assist in optimizing risk governance
Indicators that a risk is about to materialize.
Examples of KRI
- Quantity of unauthorized equipment or software detected in scans
- Instances of SLAs exceeding thresholds
- High average downtime due to operational incidnts
- How long does it take to patch/replace systems?
- Excessive average time to research and remediate operations incidents
- Number of machines that do not have current antivirus signatures or not running full system scans within scheduled periods.
KRIs Support:
- Risk appetite
- Risk Identification
- Risk Mitigation
- Risk Culture
- Risk Measurement and Reporting
- Regulatory Compliance
Risk Management Process Review⌗
Risk Assessment⌗
- Usually the most difficult
- Numerous Unknowns
- Necessary effort of gathering the right data/information of infrastructure
Risk Analysis⌗
- Can be done Qualitatively or Quantitatively
Risk Mitigation⌗
- Take steps to reduce risk to acceptable levels
Risk Monitoring⌗
Risk must be managed; it cannot be eliminated
Legal Considerations⌗
Not heavily tested due to the fact that the CISSP is now very international.
Liabilities - who is at fault?⌗
- Failure of management to execute Due Care/ Due Diligence can be termed negligence
- Culpable negligence can lead to prove liability (holding those who failed to handle risk at fault)
- Prudent Man Rule
- Perform duties that prudent people would exercise in similar circumstances
- Due Diligence; researching industry standards and best practices
- Due Care: setting and enforcing policy to bring organization into compliance(SOC, PCI, etc)
- Downstream Liabilities
- Integrate technology with other companies can extend one’s responsibility outside the normal bounds.
** Consider the Following **
A Kubernetes cluster you control is compromised by an attacker, which is used to make a substantial attack on another organization causing millions of dollars in damage. Are you liable for the damages? Maybe(?)
Can you secure a system that is impossible to breach? …No You cannot guarantee compromise protection. You can implement Due Care, and Due Diligence to protect systems. Be a Prudent person with responsibility to protect systems.
Due Diligence is the research. Due Care is the action.
Types of Laws⌗
- Criminal
- Civil
- Regulator
- Intellectual Property
Criminal Law⌗
Difficult to prosecute before a jury, so rarely result in guilty verdicts.
- Beyond reasonable doubt- difficult to meet burden of proof in computer related crimes
- Penalties: Financial, Jail-time, death
- Felonies: heaviest penalties, incarceration of at least a year
- Misdemeanors: fines & jail time(< 1 year)
- Criminal system goals: Punishment and Deterrence of future crime.