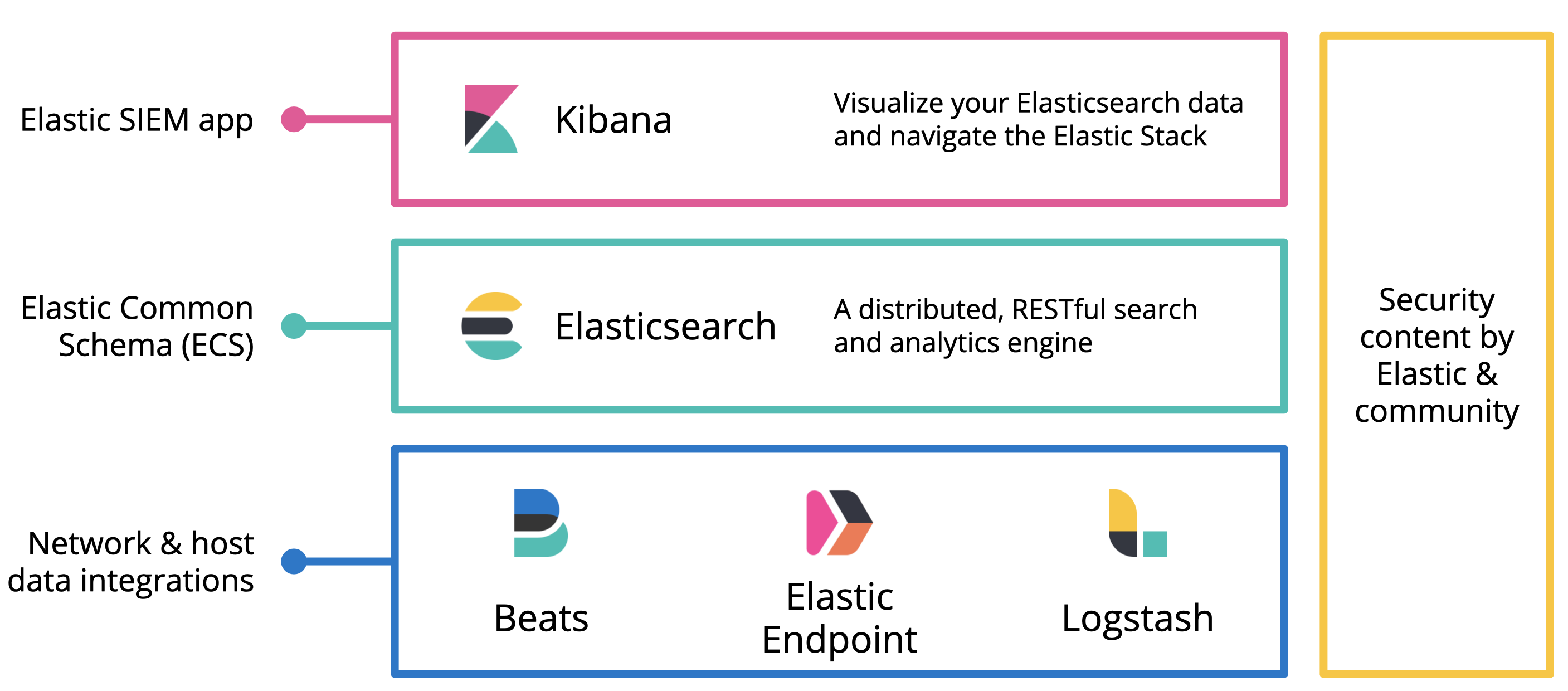
Elastic Stack SIEM Homelab
Setting up Elastic SIEM[Elasticsearch + Kibana] with secured communication in a VM homelab for experimentation and learning. This guide walks through configuration and options to assemble a functional SIEM stack to expand upon. 

Risk Definitions and Identification
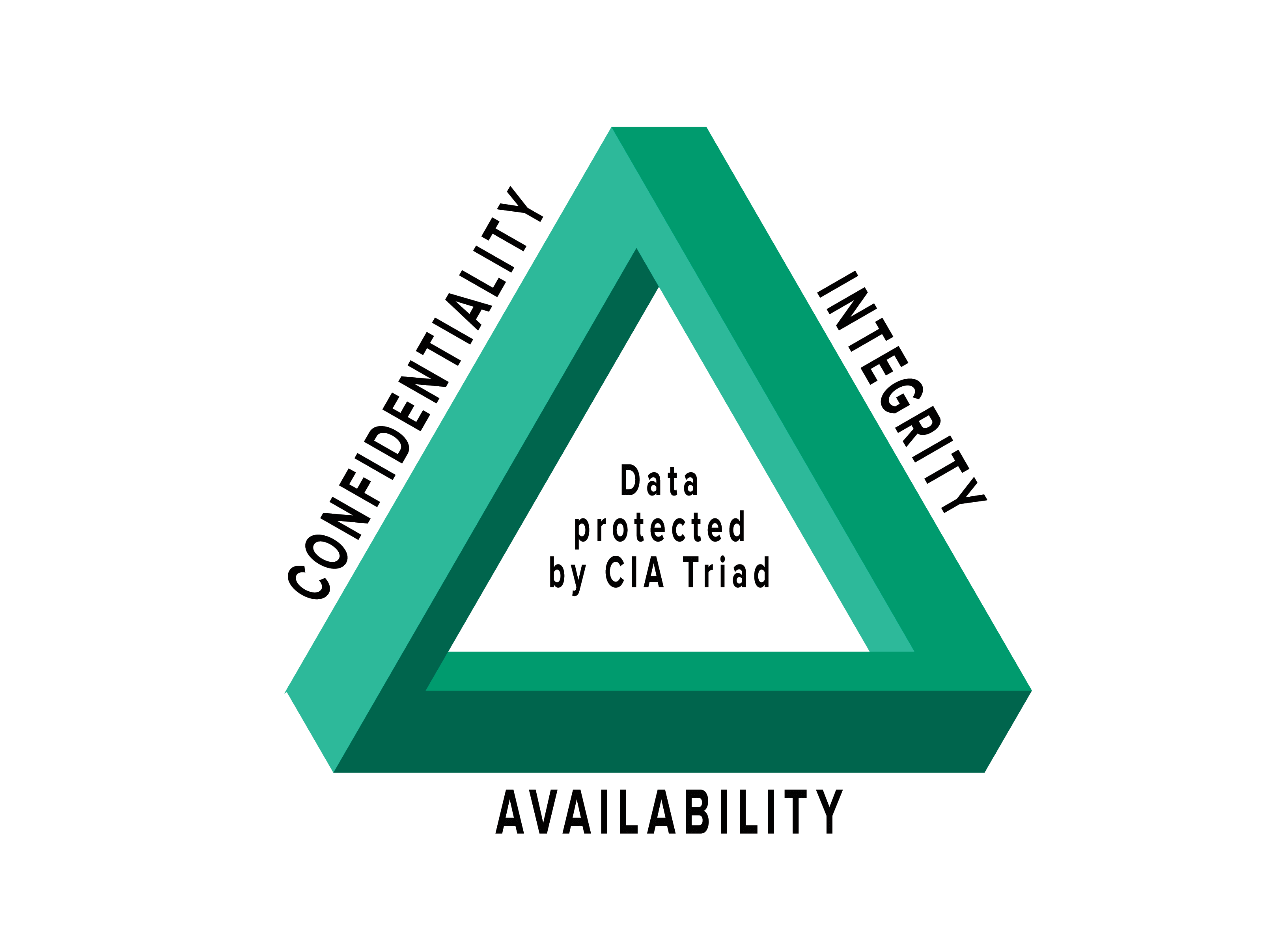
Risk Management is the foundation for all security decisions.
ISRM: Information Security Risk Management ISRM, or Information Security Risk Management is the process of managing risks associated with the use of information technology. It involves identifying, assessing, and treating risks to the confidentiality, integrity, and availability of an organization’s assets.
Managing risks associated with the IT/CIA Triad
Source
Risk Definitions Lingo for identifying risk. For the CISSP, you need to be solid on definitions since organizations use of terms can shift a bit.
GCP: Mitigating Security Vulnerabilities
Google Cloud Platform tools to mitigate various potential exploits and vulnerabilities. Dives into securing infrastructure, Network protections, Application Security, and Content vulnerabilities. Notes from Coursera course.
Oh Mongo, where art thou?
Hello dear player! Won’t you please come help me get my wish! I’m searching teacher’s database, but all I find are fish! Do all his boating trips effect some database dilution? It should not be this hard for me to find the quiz solution! Find the solution hidden in the MongoDB on this system.
Login Found Mongo’s hosted port with netstat -lntp
Then connecto to the exposed port with:
GCP: Core Services Notes
Notes from the early Coursera GCP Core part of Security in Google Cloud Platform course. Recording relevant terminology(buzzwords) and quotes from the video lectures. Not 100% complete, if there was a topic I’m very familiar with, I possibly skipped taking down long form notes. The course was useful reminder of what-does-what, so I’ll deem it worth keeping around for now. TTL=2years?
Cloud Native Security
Notes from Steve White’s OWASP PDX talk on modernizing Security for cloud native platforms.
How to Hack OAuth
BSides PDX talk by Aaron Parneki. How OAuth works, and various examples of how it has been breached.